kernel pwn基础[2]

2018 0CTF Finals Baby Kernel
这次题目的附件只有驱动和文件系统没有bzImage
1 | tcdy@arch-linux ..study_kernel/2018_0CTFFinalsBabyKernel % strings baby.ko | grep vermagic= |
1 | tcdy@196082:~/Desktop/download/study_kernel$ sudo apt download linux-image-4.15.0-22-generic |
分析驱动
1 | __int64 __fastcall baby_ioctl(__int64 a1, __int64 a2) |
首先可以看到函数分为两部分,第一部分就是打印出flag的地址,第二部分则是经过两次检验之后进入下面的逐字节对比。
1 | bool __fastcall _chk_range_not_ok(__int64 a1, __int64 a2, unsigned __int64 a3) |
这个验证函数些许看不懂,直接看汇编好一点
1 | .text:0000000000000000 55 push rbp |
就是第一个参数和第二个参数的和必须小于第三个参数
1 | && (unsigned __int8)_chk_range_not_ok(v2, 16LL, *(_QWORD *)(__readgsqword((unsigned int)¤t_task) + 4952)) != 1 |
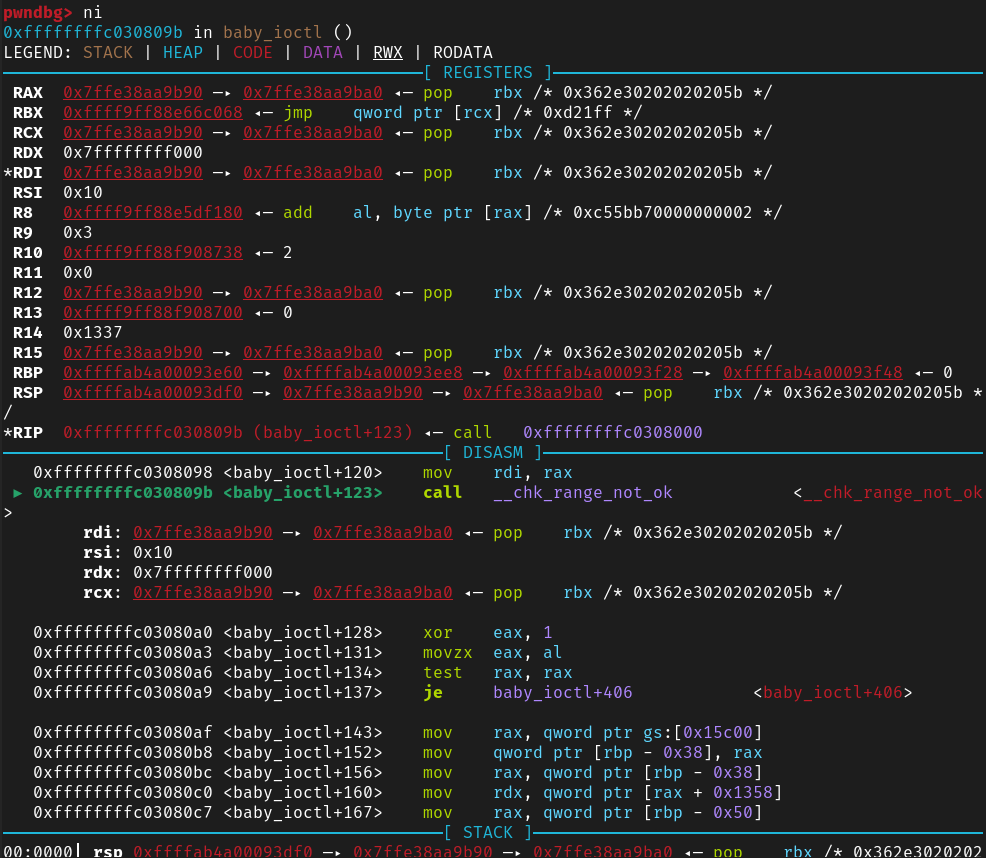
可以看到这里其实就是看看传入的参数是否是用户态
这道提分为两种利用方式,这里都提一下(毕竟我都还不会)
Double Fetch
这一利用方式可以看做是条件竞争,这里是两次验证,第一次验证是否为用户态,第二次逐字检查flag,那么要是在第一检查结束后将地址换成正真的flag地址,那么后一个验证即可绕过
1 |
|
侧信道攻击
名字虽然听起来很高端,实际干的事情就是爆破每一个字节。
方法的原理就是:创建三个段,除了中间的段可读可写外,其他段的权限都为000,那么我们将flag放到第二个段的末尾,然后将猜测的字符放到最后一个,当最后一个字符不正确的时候就会直接退出,但是当最后一个字符正确的时候就会因为权限问题报错,并且系统崩溃
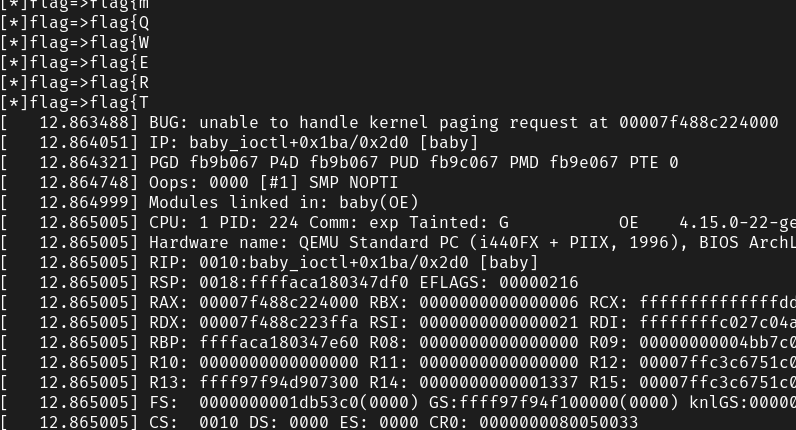
1 |
|
1 |
|
评论
评论插件加载失败
正在加载评论插件